What is Browser forensics and how to do it?
With the help of Browser Forensics and with the assistance of forensics tools one can extract sensitive data and chosen keywords from most web browsers. One can retrieve deleted data and keywords, check whether history was cleared, retrieve artifacts like Cookies, Downloads data, History, Saved Password, websites visited etc.
Where can I take computer forensics courses online?
Norwich University’s Master of Science in Information Security & Assurance online program provides individuals with the advanced skills and tools needed to succeed as computer forensics investigators, offering courses in an online format that works in conjunction with a student’s other family and work responsibilities.
What is network forensics and how does it work?
When talking about network forensics, we’re actually talking about the data that has been transmitted over the network, which might serve as the only evidence of an intrusion or malicious activity.
What is computer forensics and how does it help the government?
Computer forensics help government and law enforcement officials combat digital crimes by locating and preserving digital evidence that suggests illegal activity.
What is web browser forensics?
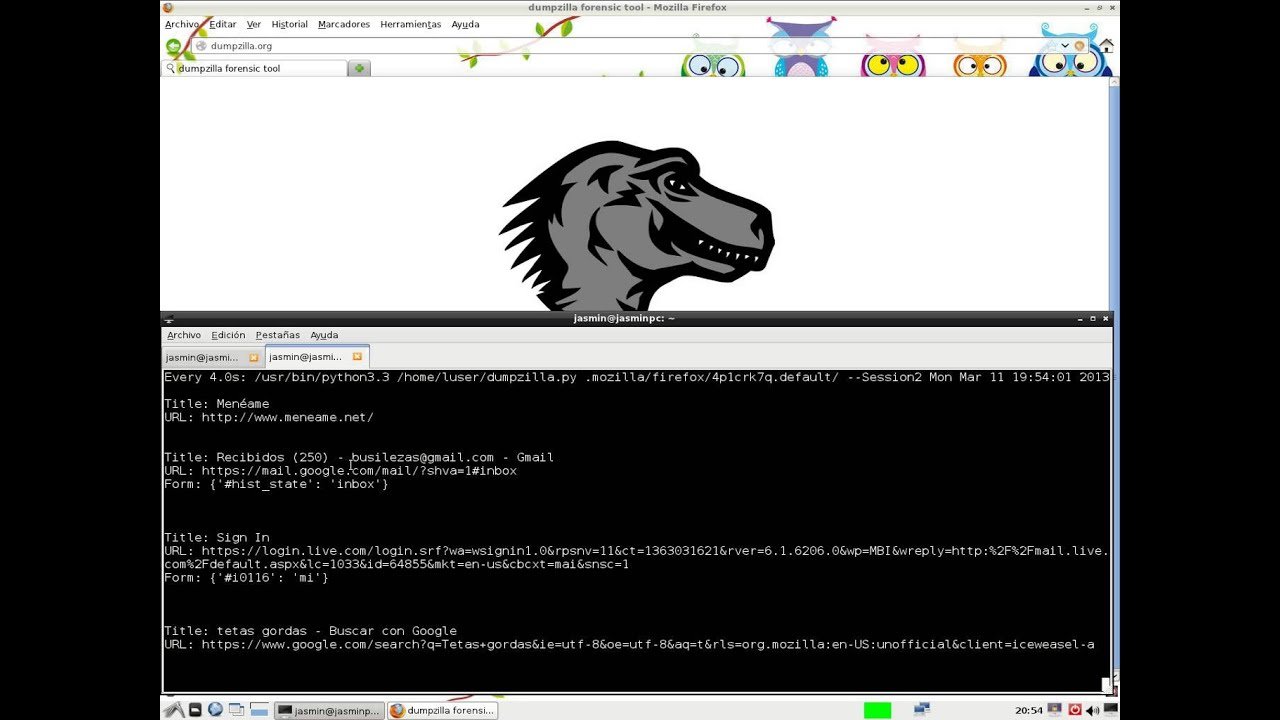
Also, Browser Forensics helps a lot to understand how an attack on a system was conducted, helping in finding the source of Malwares/Adwares/Spywares, Malicious Emails and Phishing Websites etc. There are many web browsers available like Chrome, Firefox, Safari, IE, Opera etc. depending upon the platform being used.
Which tool is used for web browser forensics?
Searching for forensic tools and techniques by functionalityWeb Browser Forensicsany Windows Mac OS Linuxany Safari Bing Toolbar Firefox Chrome Google Maps Google Toolbar Microsoft Edge Internet Explorer Opera 360 Safe Browser Xbox Internet Explorer1 more row
What is computer forensics How can it help in any field of work?
Computer forensics, also known as cyber forensics or digital forensics, is the investigation of digital data gathered as evidence in criminal cases. Law enforcement agencies and private firms fight cybercrime using computer forensics to track, locate and extract digital information needed for criminal investigations.
What are the uses of computer forensics?
In the private sector, commercial organizations use computer forensics to unearth or investigate a wide spectrum of cases such as fraud, espionage, forgeries, intellectual property thefts, employee disputes, bankruptcies, regulatory compliances, and inappropriate data usage among others.
How is data used in a forensic investigation?
Data forensics can also be used in instances involving the tracking of phone calls, texts, or emails traveling through a network. Digital forensics professionals may use decryption, reverse engineering, advanced system searches, and other high-level analysis in their data forensics process.
What is browser history Examiner?
Browser History Examiner (BHE) is a forensic software tool for capturing, analysing and reporting internet history from the main desktop web browsers.
Is computer forensics a good career?
Is Digital Forensics a Good Career? Yes, digital forensics is a good career for many professionals. According to the Bureau of Labor Statistics, demand for forensic scientists and information security analysts is expected to be very high.
What is the future demand for computer forensics?
According to data from 2019, the demand for this job is expected to grow by 32 percent from 2018 to 2028, which is extraordinarily fast. At this rate of growth, more than 35,500 jobs are expected to be added during that time period (BLS 2019).
Is computer forensics a good degree?
Is computer forensics a good degree? Yes, a bachelor's degree in computer forensics equips graduates with invaluable technical and career skills. This degree qualifies graduates for careers as information security analysts and computer forensics technicians.
Who can use computer forensic services?
General criminal and civil cases. This is because criminals sometimes store information in computers. Commercial organizations and companies can also use computer forensics to help them in cases of intellectual property theft, forgeries, employment disputes, bankruptcy investigations and fraud compliance.
What are types of computer forensics?
Types of Computer Forensics: Email forensics. Malware forensics. Memory forensics. Mobile Phone forensics.
What do computer forensic specialists do?
Computer forensic investigators help retrieve information from computers and other digital storage devices. The retrieved data can then be used in criminal investigations or as evidence in cases for cyber crimes.
What is browser investigation?
For cybersecurity analysts, a browser investigation can be a critical step in their incident response playbooks. It typically occurs after a user has crossed a predefined risk threshold (becoming “a notable user”), or after a system has been flagged as suspicious or potentially compromised. In a criminal investigation, it’s done after ...
How long does a web investigation take?
The results showed that web investigations take a significant amount of time. Most investigations took over an hour, which can add up when you consider the number of devices that must be examined during an organizational breach or a criminal investigation.
What browser is more than how you access applications and websites?
Whatever your browser preference—Chrome, Firefox, Safari, Internet Explorer, or Edge—your browser is more than how you access applications and websites. Whatever your browser preference—Chrome, Firefox, Safari, Internet Explorer, or Edge—your browser is more than how you access applications and websites. It’s also a potential cache of many things ...
Which is the most popular browser?
It’s not surprising that Chrome , which is available on every platform and is the most popular web browser in the world, took the top spot, while Internet Explorer (IE) and Firefox took second and third places, respectively. The distribution of browsers can be dependent on the host operating system, while Chrome and Firefox can run on most systems, ...
Is the browser a roadmap?
Some would say with its level of access, the browser is not only a roadmap of your personal and professional life, it’s a window into your thoughts. Law enforcement investigators have long been aware of the power of the browser to provide important information and have zealously included it in their criminal investigations.
What is browser forensics?
Browser forensics: Google chrome. Browsers have become an inherent part of our virtual life and we all make use of browsers for surfing the internet in some or the other way. Also, browsers can be used not only for surfing, we can make use of browsers for navigating through the file system of the OS. You might have observed by default browsers ...
Why is a browser important in forensics?
Thus they play a very important role in forensics due to the nature and amount of data they store with them.
What is an artifact in Chrome?
An artifact is a remnant or trace left behind on the computer which helps to identify the source of malicious traffic and attack conducted onto the system. Few examples include cache data, History, Downloads etc. Chrome stores these artifacts inside specific folders in the operating system.
Can browsers be used for surfing?
Also, browsers can be used not only for surfing, we can make use of browsers for navigating through the file system of the OS. You might have observed by default browsers store data like search queries, username, password, form data, emails, credit card data and other sensitive information.
What is computer forensics?
Computer forensics also can locate hidden documents or emails on digital devices, helping law enforcement investigators prove premeditated intent. The field of computer forensics offers significant benefits to society and broad job opportunities for individuals looking to pursue a career in this field.
What is a computer forensics investigator?
A computer forensics investigator or analyst typically conducts many tasks during an investigation. According to InfoSec’s website, these professionals examine data gathered from computers and other devices, dismantle and rebuild damaged systems to locate lost data, write detailed reports, and testify in court.
Why is metadata important in forensics?
Metadata is critical for computer forensics investigators trying to locate a suspect.
What skills are needed for forensics?
Additionally, Krehel states the importance of organization and communication skills, as well as a desire to learn, for individuals interested in digital forensics roles. Adroitness in record-keeping and verbal interaction with law enforcement professionals are crucial to succeed in computer forensics investigations.
How does education affect forensics?
Education, experience, type of company, and the geographical area also impact the earnings of a computer forensics investigator. “Digital forensics salary can increase with experience, advanced degrees, and security clearance.
How much does a digital forensic investigator make?
According to Payscale, the median salary for a digital forensic investigator is $71,850 per year. For example, information security analysts, professionals with comparable education and training to computer forensic investigators, earned a median salary of $98,350 per year in 2018, according to the U.S. Bureau of Labor Statistics (BLS).
What are the crimes that people commit on the internet?
Billions of individuals globally use digital technology daily. While most people implement it for personal or professional reasons, some individuals use the Internet to commit crimes. Phishing/spoofing, blackmail, child pornography, harassment, financial fraud, and drug and weapons trafficking are ...
1. Computer Forensics Courses and Certifications (Udemy)
This e-learning website brings you a wide array of courses on this rapidly increasing field. There is something available for everyone irrespective of their experience level. If you are thinking about jump-starting a career in this area then you may take the fundamental lessons, forensics from scratch, open source tools.
2. Digital Forensics Courses Online (Pluralsight)
With the broadening of the field of digital forensics, there are a plethora of paths to explore. So if you want to look around the various skills that can be picked in this line of work then this platform won’t disappoint you.
3. Cyber Security Courses and Training (Digital Defynd)
If you are interested in making the internet a safer place then and want to understand the mind of cybercriminals to fight the different threats then you can scout out the options available of this platform. Explore how to report the vulnerabilities across the networks, mitigate privacy issues, wireless security and more.
4. Ethical Hacking Course & Certification (Digital Defynd)
Digital Defynd brings you a series of choices to help you build a career as an ethical hacker. Take a look at the mix of industry and academic expert based courses to identify the skills that you would like to work on.
5. Learning Computer Forensics (LinkedIn Learning)
Primarily aimed at beginners, this training will help you to cover the basics of this growing and exciting field. Begin with understanding the prime goal of this area, the types of investigations it is used for, a forensic investigator’s typical toolset and the legal implications of this type of work.
Digital Forensics – Complete Digital Forensics Masterclass
The course is not free anymore, Will Update you soon once its free again, Stay tuned.
Description
Most comprehensive Digital Forensics Course, You will learn Depth understanding of how computers work and how to do digital forensics.
What is network forensics?
Network forensic analysis is part of the digital forensics branch, which monitors and analyzes computer network traffic for the purposes of gathering information, collecting legal evidence, or detecting intrusions [1]. When talking about network forensics, we’re actually talking about the data that has been transmitted over the network, ...
What does a forensic analyzer do?
The forensic analyzer must look through all the logs on the compromised service to look for forensic evidence. The forensics analyzer soon discovers that the attack was conducted from the cloud provider’s network, so he asks the cloud provider to give him the logs that he needs.
Which layer of the application is the least configurable?
The PaaS is the middle layer, which automates certain things, but is less configurable. The top layer is SaaS, which offers the least configuration, but automates a large part of the infrastructure that we need when deploying an application.
Browser Features Make Life Easier by Retaining A Plethora of User Information
Exabeam’S Survey of Digital Forensics and Incident Response Professionals
- In April 2018, Exabeam conducted a survey of digital forensics and incident response (DFIR) professionals to better understand what they are experiencing during their web browser investigations in the field. Among other things, we were interested in what web browsers they encountered during their cases, how many devices they examined a month, and how long each r…
Synopsis: An Exabeam Tool Designed to Help with Browser Investigations
- Exabeam’s open source tool called Synopsis is designed to aid investigators reviewing browser history files by providing a high-level summary of key information. Many questions are common across different types of investigations, and Synopsis helps analysts get the answers they need quickly. With the Synopsis dashboard, analysts can view an overview of data from the device in …
Resources to Aid in Your Browser Investigations
- The Exabeam survey shows us that DFIR professionals spend a significant amount of time on their web browser investigations, suggesting that making browser investigations quicker and more efficient is very needed—Synopsis is designed to help. You can click hereto download Synopsis on GitHub. How to Investigate Insider Threats Using Web Browser Forensics Blog: Ho…
Popular Posts:
- 1. who is responsible if you hit a house on a golf course?
- 2. what does tpc stand for golff course
- 3. what course number is english language and composition
- 4. how to become a millionaire course
- 5. what is the situation geography of golf course in palm desert california usa
- 6. what relevant course for auditor evaluator
- 7. course hero how would the service create value? how would each customer measure that value
- 8. ece 311 w2 d 2 why are well-qualified teachers important? course hero
- 9. learnpress how to buy course
- 10. what is done in the benedict test course