The most basic use for a TPM is to set a login password for your system. The chip will automatically guard that data, rather than keep it stored on your hard drive. If a system has a TPM chip, its user can generate and manage cryptographic keys used to lock the system or specific files.
Full Answer
What is a TPM chip?
Dec 18, 2019 · 5 . How does the TPM chip work ?25 . Why primarily are account lockout policies put into place ?
How does a TPM protect the operating system?
How does the TPM chip work? It encrypts private keys stored in the file system. It stores private keys, moving them out of the file system. It brokers connections to a network-installed hardware security module for private key storage. It brokers connections between the smart card reader and the smart card. a .
What are the benefits of the TPM?
02. CAN YOU HACK TPM CHIPS? YES Organisations that employ these technologies should consider CovertSwarm’s findings and review the associated information security risks and their impact upon their security posture. We acknowledge and expand upon the TPM work carried out by Henri Nurmi at F-Secure [1], to demonstrate a real-world attack chain against Microsoft’s …
How do TPM and BitLocker work?
Jun 25, 2021 · The most basic use for a TPM is to set a login password for your system. The chip will automatically guard that data, rather than keep …
What is TPM chip?
TPM chips also provide safe storage of encryption keys, certificates and passwords used for logging in to online services, which is a more secure method than storing them inside software on the hard drive.
Why do I need a TPM?
Many people use a TPM to enable Windows' BitLocker Drive encryption utility. When you power up a system that features a TPM and BitLocker, the chip runs a series of conditional tests to see if it's safe to boot up.
What is TPM security?
Primarily, the TPM enhances security above and beyond the capabilities of consumer software. It also can be used to keep your PC running well. Since an industry consortium called the Trusted Computing Group (TCG) introduced TPM in 2009, more than 2 billion of the chips have been embedded into PCs and other devices, such as ATMs and set-top boxes.
Is TPM 2.0 required for Windows 11?
(Image credit: REDPIXEL.PL / Shutterstock) PC makers often list a Trusted Platform Module (TPM) as a security feature for laptops and desktops and TPM 2.0 will be a system requirement for Windows 11, but you may not know what it is or why it's useful. Primarily, the TPM enhances security ...
What is a TPM?
The TPM is a cryptographic module that enhances computer security and privacy. Protecting data through encryption and decryption, protecting authentication credentials, and proving which software is running on a system are basic functionalities associated with computer security. The TPM helps with all these scenarios and more.
What is TPM security?
The security features of Windows 10 combined with the benefits of a TPM offer practical security and privacy benefits. The following sections start with major TPM-related security features in Windows 10 and go on to describe how key technologies use the TPM to enable or increase security.
What is CNG in Windows?
Windows includes a cryptography framework called Cryptographic API: Next Generation (CNG), the basic approach of which is to implement cryptographic algorithms in different ways but with a common application programming interface (API). Applications that use cryptography can use the common API without knowing the details of how an algorithm is implemented much less the algorithm itself.
What is Windows Hello for Business?
Windows Hello for Business provides authentication methods intended to replace passwords, which can be difficult to remember and easily compromised. In addition, user name - password solutions for authentication often reuse the same user name – password combinations on multiple devices and services; if those credentials are compromised, they are compromised in many places. Windows Hello for Business provisions devices one by one and combines the information provisioned on each device (i.e., the cryptographic key) with additional information to authenticate users. On a system that has a TPM, the TPM can protect the key. If a system does not have a TPM, software-based techniques protect the key. The additional information the user supplies can be a PIN value or, if the system has the necessary hardware, biometric information, such as fingerprint or facial recognition. To protect privacy, the biometric information is used only on the provisioned device to access the provisioned key: it is not shared across devices.
What is device encryption?
Device Encryption. Device Encryption is the consumer version of BitLocker, and it uses the same underlying technology. How it works is if a customer logs on with a Microsoft account and the system meets Modern Standby hardware requirements, BitLocker Drive Encryption is enabled automatically in Windows 10.
What is a credential guard?
Credential Guard is a new feature in Windows 10 that helps protect Windows credentials in organizations that have deployed AD DS. Historically, a user’s credentials (e.g., logon password) were hashed to generate an authorization token. The user employed the token to access resources that he or she was permitted to use. One weakness of the token model is that malware that had access to the operating system kernel could look through the computer’s memory and harvest all the access tokens currently in use. The attacker could then use harvested tokens to log on to other machines and collect more credentials. This kind of attack is called a “pass the hash” attack, a malware technique that infects one machine to infect many machines across an organization.
What is Windows 10 security?
The Windows 10 operating system improves most existing security features in the operating system and adds groundbreaking new security features such as Device Guard and Windows Hello for Business. It places hardware-based security deeper inside the operating system than previous Windows versions had done, maximizing platform security while increasing usability. To achieve many of these security enhancements, Windows 10 makes extensive use of the Trusted Platform Module (TPM). This article offers a brief overview of the TPM, describes how it works, and discusses the benefits that TPM brings to Windows 10—as well as the cumulative security impact of running Windows 10 on a PC that contains a TPM.
What is a TPM chip?
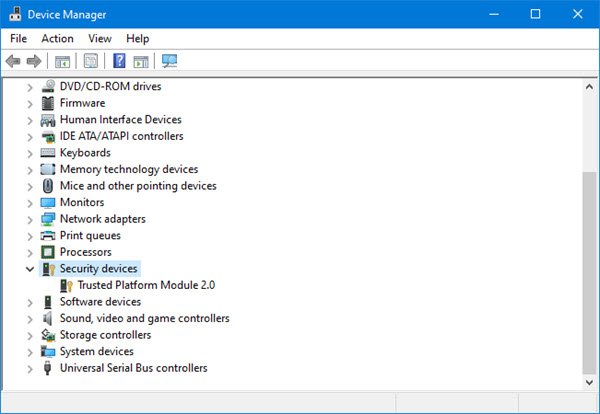
Trusted Platform Module (TPM) technology is designed to provide hardware-based, security-related functions. A TPM chip is a secure crypto-processor that is designed to carry out cryptographic operations. The chip includes multiple physical security mechanisms to make it tamper resistant, and malicious software is unable to tamper with the security functions of the TPM. Some of the key advantages of using TPM technology are that you can: 1 Generate, store, and limit the use of cryptographic keys. 2 Use TPM technology for platform device authentication by using the TPM’s unique RSA key, which is burned into itself. 3 Help ensure platform integrity by taking and storing security measurements.
Why is TPM good?
This is good to mitigate phishing attacks because it prevents the key from being copied and used without the TPM. TPM-based keys can also be configured to require an authorization value to use them.
What is antimalware software?
Antimalware software can use the boot measurements of the operating system start state to prove the integrity of a computer running Windows 10 or Windows Server 2016. These measurements include the launch of Hyper-V to test that datacenters using virtualization are not running untrusted hypervisors.
What is device health attestation?
Device health attestation enables enterprises to establish trust based on hardware and software components of a managed device. With device heath attestation, you can configure an MDM server to query a health attestation service that will allow or deny a managed device access to a secure resource.
Can a TPM be exported?
After a computer is provisioned, the RSA private key for a certificate is bound to the TPM and cannot be exported. The TPM can also be used as a replacement for smart cards, which reduces the costs associated with creating and disbursing smart cards.
Does Windows 10 have a TPM?
Starting with Windows 10, the operating system automatically initializes and takes ownership of the TPM. This means that in most cases, we recommend that you avoid configuring the TPM through the TPM management console, TPM.msc. There are a few exceptions, mostly related to resetting or performing a clean installation on a PC. For more information, see Clear all the keys from the TPM. We're no longer actively developing the TPM management console beginning with Windows Server 2019 and Windows 10, version 1809.
What is a TPM?
The Trusted Platform Module (TPM) is a special purpose microcontroller designed by the Trusted Computing Group, which interfaces with a standard hardware/software platform in order to allow it to be secured to serve the interests of just one party - the system designer.
What is TPM hash?
The TPM does make extensive use of cryptographic hash operations, however, and currently uses the SHA-1 hash algorithm. This hash algorithm is used to "extend" the values in the Platform Configuration Registers (PCRs), to detect and prevent data modification, identify keys, and to create "capabilities" used to improve the efficiency ...
Popular Posts:
- 1. how long is a driver improment course
- 2. how were the american people able to closely follow the course of the mexican-american war?
- 3. what does it cost to have bridal shower at shale creek golf course
- 4. when do results of basic rider course get sent to dmv
- 5. how do i report my child taking a college course in high school on my taxes
- 6. course hero how will an open port respond to an xmas scan
- 7. 1. a description of how course hero serves students and how the knowledge drive supports this.
- 8. what do the 'good genes hypotheses' propose? course hero
- 9. when assembling teams for the nrp provider course ideally an instructor should
- 10. which of these are owners with an exit plan? course hero